The August 9 2016 security update for Office 2013 included a non-security feature to allow administrators to use Group Policy to block macros from running in files that are downloaded from the Internet. This feature was added to Office 2016 earlier this year.
This policy can be enabled using Group Policy or by editing the registry. With this policy set, macros in files downloaded from the Internet are blocked, even if the Macro Security settings allow macros to run and the Enable Editing button is clicked.
After clicking Enable Editing a new banner tells the user that macros are blocked:
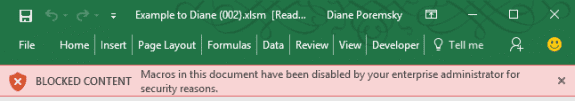
This setting will apply to documents downloaded from Internet websites, consumer storage providers (OneDrive, Google Drive, and Dropbox) or from public shares on the Internet (file-sharing sites), and attachments to emails that were received from outside the Exchange organization,
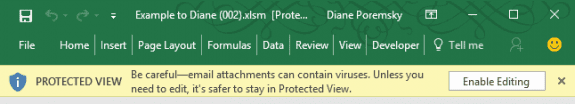
If you use Protected View, is this necessary? Yes! Only one person needs to disable Protected View on an infected document to infect the entire network. It's an additional roadblock but is not foolproof, as there is a way around it: if the Office file is saved to a trusted location or was previously trusted by the user, macros will be allowed to run, but may delay the user long enough to realize a file is not legitimate. I recommend everyone use it.
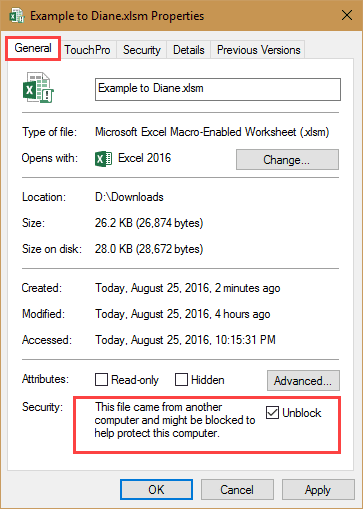
To trust a document, select the file in Windows Explorer, right click and choose Properties. Click Unblock.
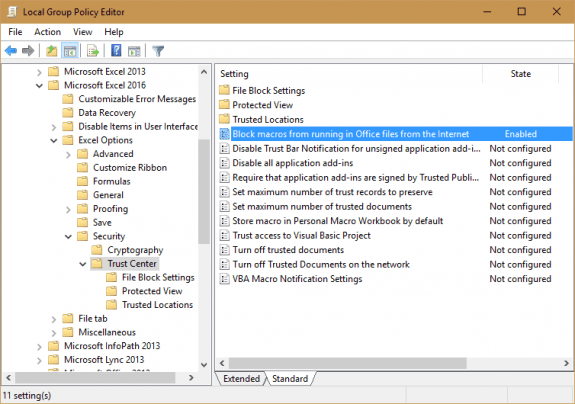
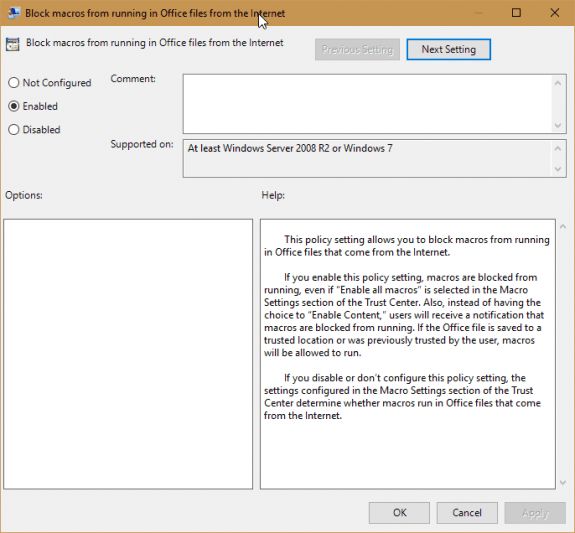
Administrators will need to enable this feature separately for Word, Excel, and PowerPoint - there isn't a single policy that applies to all Office applications. In the Group Policy Editor, it's under User Configuration > Administrative templates > Microsoft [application] 2016 > [application] options > Security > Trust Center.
Open the Block macros from running in Office files from the Internet setting and select Enabled then click OK.
To enable this setting by editing the registry, create a DWORD named blockcontentexecutionfrominternet under each of the following keys and set the value to 1.
If the keys don't exist, you'll need to create them.
Office 2016
HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\office\16.0\word\security
HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\office\16.0\excel\security
HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\office\16.0\powerpoint\security
In each key listed above, create this value:
DWORD: blockcontentexecutionfrominternet
Value = 1
Office 2013
HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\office\15.0\word\security
HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\office\15.0\excel\security
HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\office\15.0\powerpoint\security
In each key listed above, create this value:
DWORD: blockcontentexecutionfrominternet
Value = 1
If you don't want to edit the registry, you can use these reg files to add the keys to your version of Outlook.
Office 2016 Office 2013
More Information
The Office 2016 Group Policy templates can be downloaded from Office 2016 Administrative Template files (ADMX/ADML) and Office Customization Tool and Office 2013 templates are here: Office 2013 Administrative Template files (ADMX/ADML) and Office Customization Tool
HELP! I tried the 2013 solution you listed here but I can still run macros. Can you please list exactly where in the registry is the DWORD supposed to go. Lastly, Does the GPO have to be enabled on the domain in order for the registry fix to work?
Thank you all your help.
You need to add the DWORD blockcontentexecutionfrominternet with a value of 1 to the following keys:
HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\office\16.0\word\security
HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\office\16.0\excel\security
HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\office\16.0\powerpoint\security
You don't need to be using GPO - just adding these keys will work... but if you use the Home or Personal suite, these keys may not work. Also, because they are in Policies, you need to restart Outlook.
What is the actual Policy Path and policy setting name that I could use to create the GPO? Thanks!
It's in the office templates at User Configuration > Administrative templates > Microsoft [application] 2016 > [application] options > Security > Trust Center and the keys that are set are listed on the page?
Thanks for this post Diane.
I wonder if there were any similar changes to outlook 2013 security recently.
Here's why :
Since a few days, our Outlook 2013 user (not all of them, but quite a few) have reported that Outlook shows a message that the macros are disabled.
VBAProject.otm is signed with a SHA256 Symantec Code Signing Certificate (valid until aug 2017) [timestamped on a SHA1 server], and with Outlook 2013 Macro Security setting "Warnings for signed macro's", users never had this issue before [we are trusted publisher on the users pc]
I have no idea why Outlook suddenly behaves differently. New complaints keep rolling in ... only from users on Outlook 2013. Other versions, 2007 .. 2016, don't seem to be affected by this issue.
Setting the Outlook 2013 Macro Security setting to "Warnings for all macros" is the only way I can get the macros to work again. But that requires the users to click "Enable", at least the first time they run a macro.
Any suggestions ?
Many thanks.