A virus infected email is making the rounds, purportedly from Microsoft, updating their service agreement. It looks like the real message but the URLs point to another site, typical of a phishing scheme. The real Microsoft service agreement email's links point to urls like //email.microsoft.com/Key-9850701.C.CFC8.G.KK.nCdd9Wk, which redirects to a legitimate Microsoft webpage.
At least one version of the infected message includes an embedded external HTML file: <img src="//{infected-site}/index.html">
The problem? When you download external content, either automatically or per message, that file will be saved to the hard drive and it will be rendered in Outlook. In this case, the HTML file is going to be rendered. While Outlook renders HTML in the Restricted zone, it appears this week's Java exploit may be able to run the Java applet in the embedded HTML. (I'm investigating this angle.)
When you view a message (either in the reading pane or open message) and allow external content, the content is downloaded and stored in the Temporary Internet Files folder (type shell:cache in Windows Explorer address bar) and displayed in Outlook. When the file is saved to the
As one of the complainers who helped convince the Outlook team we needed the ability to block web bugs, my recommendation is never download content automatically. Don't trust external content from any address.
Don't download external content by default. No exceptions. Don't trust anyone.
With external content blocked by default, mail loads faster, web bugs aren't sent back to the sender and most importantly, blocking external content may prevent this java exploit from infecting your computer.
Messages sent with external content are almost always "bulk mail" - messages from advertisers and spammers. In most cases, the blocked content is a logo and style sheets, adding eye-candy but not content. You won't miss much by not downloading this content. In the case of advertisements that are all images, you can easily download the content when the message subject or text in the body is enticing enough to convince you that the blocked content is worth reading. (Take note advertisers: use more text, fewer external images!)
If you block external content *and* do not trust anyone, the HTML will not download and the Java definitely won't run.
Reading all mail in plain text is also an option. This is less desirable in my opinion: HTML messages displayed as plain text are harder to read and you will display more messages in HTML than you will enable external content on. It doesn't increase your security by an appreciable amount. Comparing cost (time spent enabling HTML per message) vs benefit (no risk compared to small risk), blocking external content has a good ROI.
In addition to blocking external content, these recommendations will help to increase your safety:
- Always hover over hyperlinks before clicking and ensure they are pointing you to legitimate sites before clicking. Look closely at the urls to insure they are not trying to fake you out with "microsoft.com.spammer.com" addresses.
- Look at the message's Internet headers if you aren't sure the message is legitimate.
- Consider disabling Java. It's too full of holes.
- Keep your antivirus and antimalware up to date.
Recommended settings for external content
To block external content in Outlook 2010 and up, go to File, Trust Center, Automatic Downloads. My recommendation: don't download any content and always warn before replies.
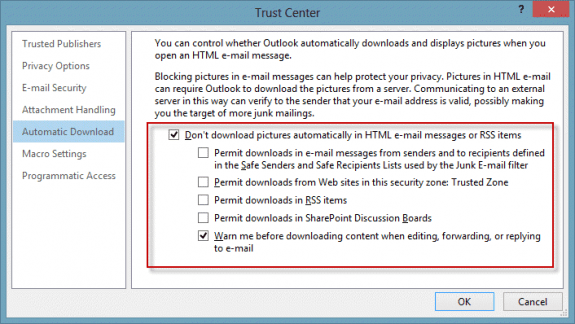
(If you want to read all mail in plain text, the setting is on the E-mail Security tab.)
In Outlook 2007, block content from the Tools, Trust Center menu.
Enable blocked content per message
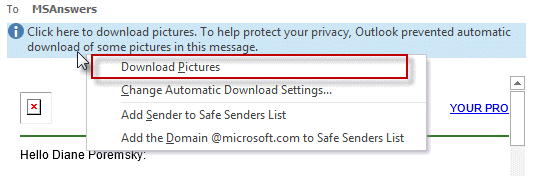
When you are reading a message and want to view the content, click on the Infobar and download external content for that message. You only need to do this once per message, Outlook will remember until the Temp Internet Cache is emptied.
More Information
How do I set the preview screen to use text vs. HTML mode Discussion at Microsoft answers forum discussing the Java exploit
Blackhole targeting Java vulnerability via fake Microsoft Services Agreement email phish
Outlook 2016 does not appear to have the "Permit downloads from Web sites in this security zone: Trusted Zone" in the Automatic Downloadstab under Trust Center, as it did in Outlook 2010. Any idea why, and whether there is an equivalent option in Outlook 2016 that can be disabled to prevent downloading of images from external sites?
I have it in my outlook 2016 - this is in the newest insider build - build 1801.
Which build/version do you have? It's possible it was temporarily removed from a build.
Good tips. However, by enabling only downloads from trusted senders in the Outlook settings surely deals with this issue, or not?
Not necessarily. If an exploit sends mail using a faked address of a trusted contact or infects a trusted person or company's computer and send mail from them, you are at risk. Because everything has to come together just right (use outlook, trust their address, mail gets past content scanners etc), the risk may not be much but its not zero.
If you don't have java installed, there should be no additional risk as the danger is in an exploit that can bypass normal security measures and at this time, only java exploits can do this.